Whenever I saw an
"injustice"
I would create
"unique things"
to
"Balance the Equation"
with
Research, Analysis, POCs and Developments
Happy, Happy, Joy, Joy
:)

" NOTE "
Since I've signed hundreds of NDA's (Non Disclosure Agreement),
I will continue to not disclose or violate any agreement(s)
which are still valid, in perpetuity, can cause intellectual property infringement(s), propriety data theft,
wink, wink, nudge, nudge, say no more, say no more... :o
Lamentably...
As with most of my
POC's, heutagogical R&D, TOADDs, or Tech,
once I would see a calamitous or foreseeable (potential) abuse
in "real world" entanglement(s)...,
they were all abruptly
terminated
and
buried
within the
"Ark of the Covenant" ...
(2014-2016)
Nefarious Ways
was an algorithmic set of protocols
on onion servers to specifically
"brake the encryption chain..."
which allowed her executables
to find criminals and predatory pedophiles,
who cowardly hid behind the veil
of encrypted apps and programs.
Unfortunately,
our current set of
"antiquated laws"
actually
protect predatory pedophiles
and criminals from persecution,
NOT their victims
or the innocent children.
:/
"NefariousWays"
was just another one of my R&D projects,
which I did as a knee jerk reaction
"to protect the innocent.'
But because of her inherent automated function(s)
and our current "antiquated laws,"
she was regrettably terminated
and now lives next to the
"Ark of the Covenant"...
for
"Embedded Journalists"
(2005-2013)
For over seven years
I gave Journalists the ability to
report and send Text and Images
during civil unrest, from within blocked, restricted,
or Geo-restricted areas or countries like:
the Gaza Strip,
Homs Syria,
Turkey,
etc...;
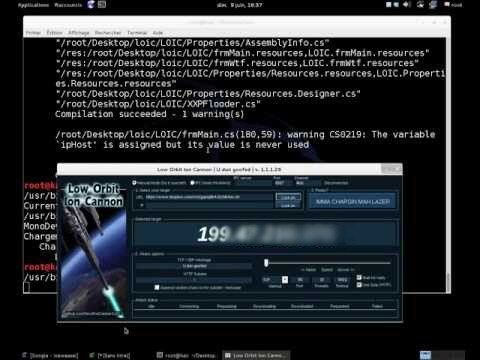
all by simply using
"Frequency Jumping"-not reliant on WiFi/Cell
and using a segmental modified LOIC & JS LOIC hack/technique...
" Noʻu ka hauʻoli "
World! :)